Are zero-knowledge proofs (ZKPs) the future of blockchain?
Innovation has exploded across the ZKP ecosystem, driven by renewed interest in consumer data privacy and the evolution of zero-knowledge Ethereum Virtual Machines (zkEVMs).
Imagine a secure internet, where your personal details are safeguarded from the moment you login. On this new internet, your data stays within the confines of your own device, putting you in complete control of your information and eliminating the fear of breaches or fraud. We believe a future internet infrastructure that prioritizes security and privacy might be closer than anticipated.
Today’s web infrastructure is designed to extract data out of every interaction and store it in centralized data storage. Companies then use this data to analyze users’ online behavior and to target them with ads likely to drive profit, with little value for the users. Of course, data sharing is also essential to the functioning of many internet applications today. From search engines to social media platforms, to ecommerce sites, data sharing enables a wide range of online activities we rely on in our daily lives.
But many internet users have an increasing interest in a private internet. This will require a new infrastructure, where users do not share their data with applications by default, but can still benefit from network-driven online applications. This can occur through computations performed on the client side, then proved to a central entity or computer. Zero-knowledge proofs (ZKPs) and protocols are the leading candidate to become the base-layer of the new internet infrastructure, where privacy is the default.
This isn’t just a futuristic pipe dream; momentum is gaining in the space. Steel DAO’s newly minted crypto research division has been tracking the sector, and has seen over $725 million in funding directed toward zero knowledge “pure-players” (i.e., companies exclusively building zero knowledge proof solutions) in 2022. The two biggest rounds were Aleo and Matter Labs’ $200 million financings, followed by Aztec’s $100 million round. Other names include Scroll, RiscZero, Elusiv and Mina Protocol.
In this article, we’ll define what ZKPs and zkEVMs are, and then examine three main categories of innovation within the category: privacy, scalability, and novel applications. We’ll explore both their potential and hurdles to overcome.
What is a ZKP?
A ZKP is a method of validating a statement or a computation without revealing anything about the statement itself. For example, if a website that sells alcohol to consumers wants to validate that a consumer is over the age of 21, a ZKP can answer that “yes” or “no” question without revealing the consumer’s actual age, or any other identifying information. More generally, ZKPs involve two parties: the prover and the verifier. The prover is the party responsible for proving a claim, while the verifier is tasked with validating the claim. These proofs are solved via computationally intensive mathematical equations, first studied by MIT researchers Shafi Goldwasser and Silvio Micali, as well as Charles Rackoff from the University of Toronto.
Although these proofs are intrinsically technical, the use cases they help solve are actually quite quotidian in nature. Take for example, the real-world case of applying for a loan. In today’s world, an applicant would have to disclose their proof of funds, credit score, and other relevant information to the bank to prove that they are eligible. The applicant is required to trust the bank not to misuse sensitive and personal information. But with ZKPs, people can apply for a loan without disclosing any sensitive data. This has the potential to fundamentally change how we deal with privacy in both the real and virtual worlds, scale existing base chains, and advance other “niche” (today) applications (e.g., decentralized AI).
We believe three factors are required to drive adoption of ZKPs in the coming years:
- Improvements in zero-knowledge Ethereum Virtual Machines (zkEVMs)
- Increased awareness and demand for data privacy from users
- Continued usage of Layer-2 scaling solutions
What are zkEVMs and why should we care?
zkEVMs are EVM-compatible virtual machines that can run ZKP computations. Ethereum Virtual Machines (EVMs) are the environment in which smart contracts on Ethereum are deployed. In other words, ZKPs can now interact with smart contracts on Ethereum, which enables broader, privacy-enabled use cases to be developed, including ZK-rollups. Rollups are a scaling solution through which multiple transactions are processed off-chain and then batched into a single transaction on Ethereum, reducing the cost and time it takes to process them. Before this, ZKPs were not compatible with smart contracts on Ethereum and had to be developed for specific applications (e.g., payments, token swaps.) We will take a closer look at how ZKPs are being used for privacy and scalability herein.
Privacy
A key mathematical property of ZKPs is that the verifier can verify the correctness of the statement in a zero-knowledge manner. Today’s applications require the transfer of data from local machines to central servers to perform computation. Even though ZKPs are gaining popularity predominantly within the crypto community, the applications of ZKPs extend far beyond the small territory of blockchains. In fact, large technology companies have already joined the game by claiming large numbers of patents relating to ZKPs. Between 2010 and 2021, Alibaba issued 1,111 ZKP patents. Other key players such as Tencent (382 patents) and IBM (225 patents) followed in the race to put a stake in the ground. Both Alibaba and Tencent are particularly focused on the financial services use cases for ZKPs, as they could become core infrastructure for many bank processes of authenticating customer identity during onboarding, loan processing, opening of investment accounts, etc. We’re convinced that the pace of innovation and change within ZKP tooling and infrastructure will influence how we interact with applications that have virtual and real-world workstreams in three major ways.
1. Account login
All applications today store passwords to authenticate users. Although Secure Remote Password Protocol (SRPP) using ZKPs has been available for quite some time, we have yet to see a startup leverage this technology for the masses and put themselves in competition with Okta. This is because web applications are written in Javascript, and it has been hard to write SRPP on web applications due to immature developer tooling. We believe it’s possible to re-design the authentication flow for widely used applications using a zero-knowledge proof that proves to the application that you have the password to your account.
2. Payment applications
Today’s ecommerce websites accumulate financial data that can be used later for other purposes that don’t benefit the customer. Although it sounds optimistic, we believe there is white space to build standardized payment APIs that do not disclose the user’s data and instead facilitates payments in a completely zero-knowledge manner. Think Aztec, a privacy-first layer 2 scaling solution, but for regular internet payments.
3. Authenticating identity in virtual and physical interactions
In almost every online and real-world interaction, users need to authenticate their identity. When applying for a visa, for instance, bank statements, passports, and other sensitive data must be provided to third parties. Instead, through ZKPs, when you apply for a visa, it could only give a “yes” or “no” answer to governmental agencies as to whether or not you have the required documents. Similarly, when buying cryptocurrency online, we need to send our “passports” and other sensitive documents to a third party that performs KYC/AML checks. Companies such as Notebook Labs are using ZKPs to ward off bad actors from interacting with decentralized finance (DeFi) protocols. The company does this by issuing tokens to compliant users, verified via ZKP, so other protocols know that these users are compliant without seeing the users’ documents.
We are excited about the ZKP use cases outside of the blockchain realm, though we recognize they are uniquely able to scale because of blockchains. Moreover, blockchains, by design, are anonymous, but they are not privacy-preserving at all, where all transactions are fully transparent. We believe Aleo, a privacy-preserving blockchain, will be able to unlock this.
Aside from increasing demands for privacy from users, there is also the need to solve for scalability. Layer 1s, like Ethereum, face the “scalability trilemma,” in which tradeoffs between scalability, security, and decentralization must be made. For example, Ethereum has the vision to remain as secure and decentralized as possible, which comes at the cost of scalability, but at the same time, its increasing popularity has caused slower transactions and non-viable fees. To this end, zero-knowledge proofs can also be used to improve scalability.
Scalability
Blockchains, like Ethereum, can be scaled either by increasing the transaction capacity of the blocks, which brings along its own set of risks such as making them more difficult to verify, or by interacting with them in different ways, such as processing transactions off-chain in batches and submitting them as an individual transaction to the main network. The networks on top of Ethereum that are implementing this approach are called L2 scaling solutions. They allow developers to build applications that live in the Ethereum ecosystem to leverage its security, decentralization, and network effects, but at higher transaction throughput and viable prices.
These solutions, also known as rollups, come in two forms: optimistic and zero-knowledge. Optimistic rollups are “fraud proofs,” meaning that batched transactions are assumed to be valid for a 7-day period (known as the challenge period) in which anyone can dispute the validity of the underlying transactions. Zero-knowledge rollups, on the other hand, don’t assume that transactions are valid by default and instead act as “validity proofs,” verifying that the underlying transactions are valid. They rely on their own mathematical property of soundness. Soundness refers to the mathematical guarantees that if the statement is false, no cheating prover can convince an honest verifier that it is true, except with some small probability. This is guaranteed through well-studied cryptographic assumptions and verifiable computation, which makes it very hard for the prover to cheat the system by malicious ways such as changing the inputs.
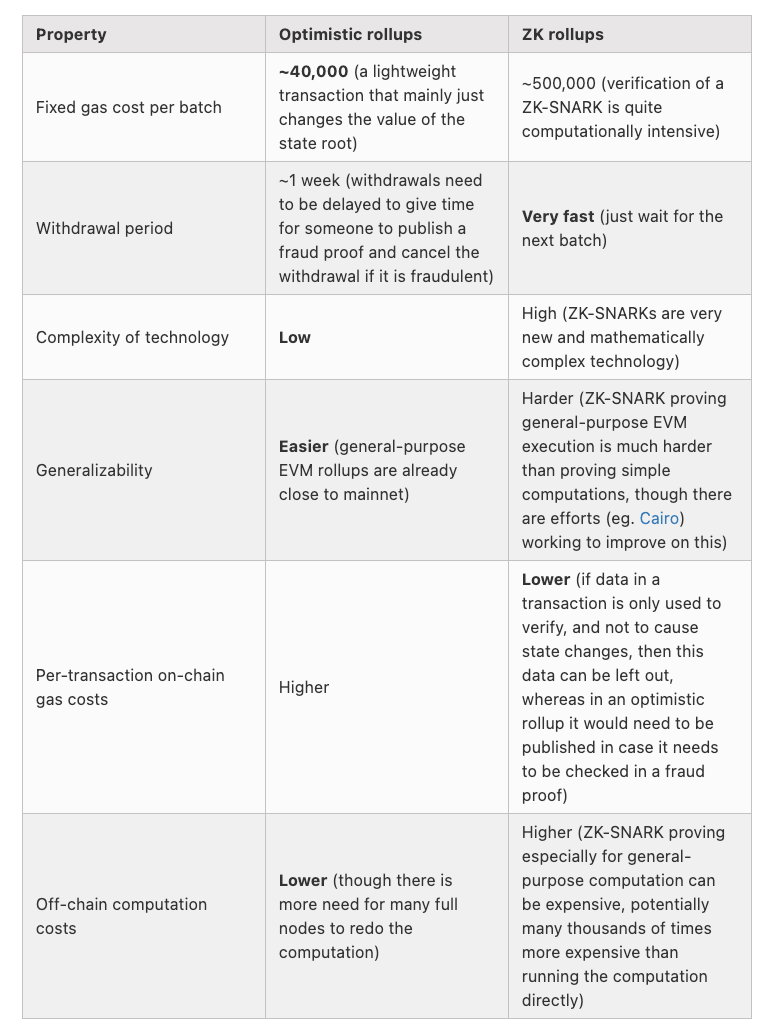
Source: Vitalik.ca
ZK-rollups can process transactions faster and do not require a 7-day challenge period like optimistic rollups do. As such, users don’t have to wait seven days before being able to withdraw their funds. Despite this, optimistic rollups currently dominate the layer 2 scaling market with roughly 80% of Total Value Locked (TVL). Historically, zero-knowledge proofs were not compatible with smart contracts. Therefore, applications built with ZK-rollups could only work for limited, application-specific use cases like dYdX, a layer 2 decentralized exchange, and Loopring, a protocol for payments and trading. As such, developers have instead opted for optimistic rollups given their compatibility with general-purpose applications.
Today, such historical limitations are being solved given improvements to zkEVMs. Now general-purpose applications can leverage the security and efficiency of ZK-rollups as their compatibility with EVMs allow them to interact with smart contracts. Therefore, we believe that ZK-rollups are poised to take over the L2 scaling market within the next few years, particularly enabled by those building the infrastructure tooling to improve the experience of developing general-purpose applications with zkEVMs, like StarkWare, Polygon, MatterLabs, and Scroll.
With that being said, zkEVMs remain relatively novel and are still being built with differing levels of Ethereum-compatibility and, in turn, performance. Broadly speaking, the highest level of compatibility is (1) Ethereum-equivalent, and the lowest level is a (4) environment in which the smart contract code (e.g., Solidity) is compiled to a language that is ZK-friendly. For example, those working on achieving the highest level of compatibility, like Ethereum’s research arm Privacy & Scaling Exploration, are doing so at the cost of performance, as their purpose is not necessarily becoming production-ready in the near future.
On the contrary, companies like StarkWare have deployed StarkNet, which is considered one of the fullest featured and highest performing zkEVMs, but which required using a new native programming language, Cairo, to support ZKP computations on EVMs. As such, it necessitates developers to learn how to execute their smart contract code in a custom environment, presenting a challenge for adoption. Projects like Polygon’s Hermez, Matter Labs’ zkSync2.0, and Scroll are looking to address these areas of friction to broader developer usage.
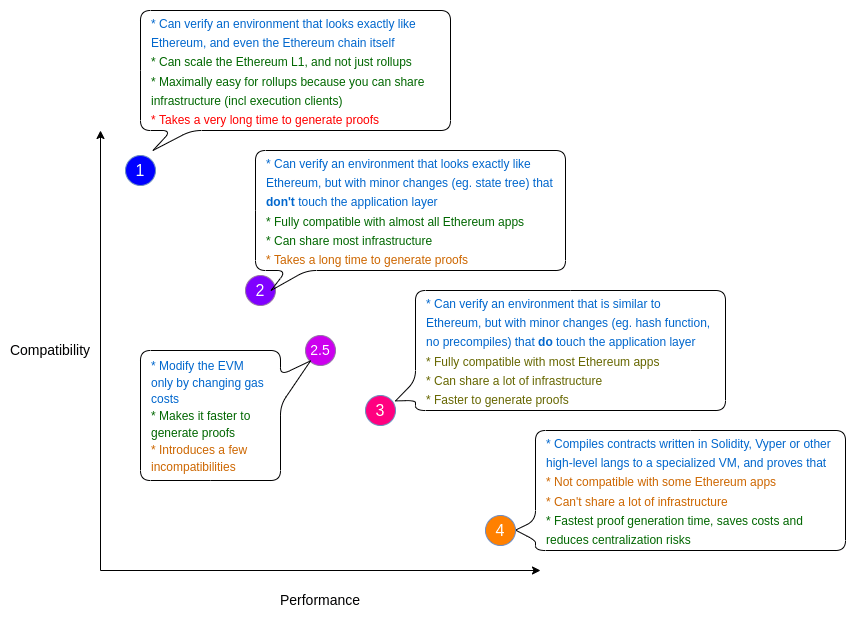
Aside from further improvements on zkEVMs, there are other challenges to increasing adoption of ZKPs that include having better infrastructure and reducing the complexity behind understanding and using them.
Hurdles to overcome
On the hardware side, builders need to either improve graphic processing units’ ability to parallel process or design specific hardware i.e., ASICs, to continue reducing the amount of time and resources it takes to prove a statement.
Although there have been many improvements on the mathematical algorithms themselves, such as the introduction of PLONK, we believe new ones will continue to emerge ultimately enabling faster, better solutions. More abstraction layers also must be built if we want the space to really take off. Although it has attracted the attention of many developers and users, generally speaking, it still remains a considerably complex space to build in and interact with.
Finally, given the natural complexity of ZKPs, regulators and even users will likely tread lightly—e.g., the recent ban on Tornado Cash reinforces the false perception that all seeking anonymity are pernicious actors.
Despite the hurdles, we’re excited for how companies are overcoming these obstacles in different, innovative ways.
Novel use cases
While ZKPs were introduced in 1989, the increased popularity of cryptography has fueled innovation and a significant rise in horizontal use cases and applications in the past few years. For example, Filecoin, a decentralized storage provider, uses PoRep, or proof-of-replication to verify that storage providers are indeed storing the data they claim to be storing. Through the usage of ZKPs, verifiers can validate this information faster without compromising security, trust, or confidence.
Another exciting application is gaming, where on-chain games like Dark Forest are leading ZKP-based innovation. One of the core features is what game theorists call “incomplete information,” where most of the virtual universe is hidden unless the player explores it. Another key feature is that players can explore this universe by sending proofs to the blockchain that the move is valid, but without revealing their coordinates in the universe.
Finally, Chainlink and Teller are working on a proof-of-concept for undercollateralized lending. In summary, Teller proves that a user’s off-chain bank account has a balance exceeding a dynamic threshold specified by the requested loan amount, without actually revealing the details of their bank account.
ZKP market map
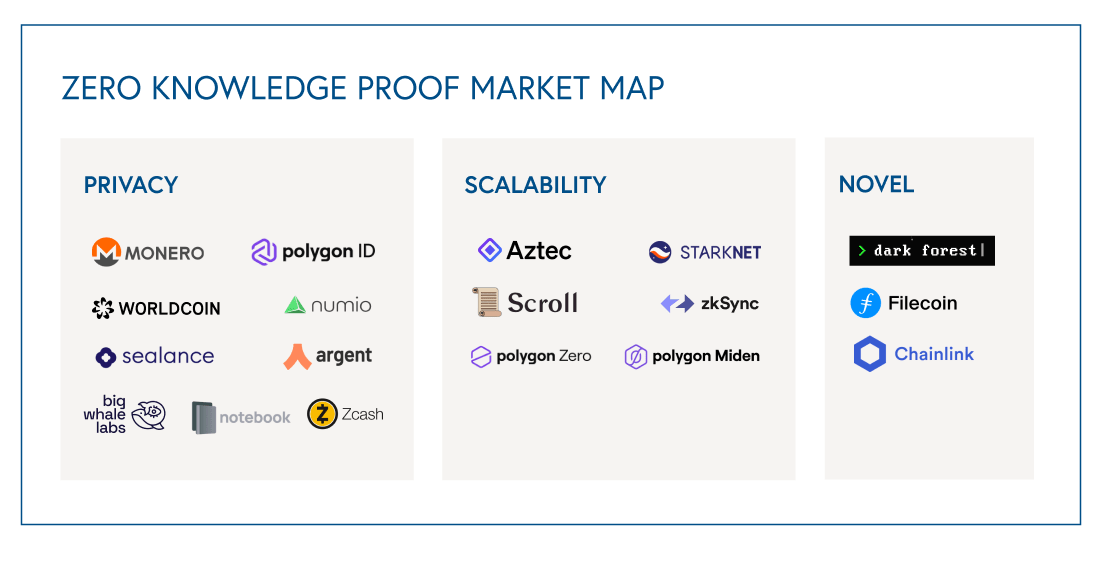
Non-exhaustive market map of the Zero Knowledge Proof landscape.
The future of ZKPs is bright
Despite the winter, crypto infrastructure will continue to evolve and advance. The emergence of "spring" feels like a nearing reality as developer activity remains robust and enterprises continue investing in both backend and consumer-facing crypto opportunities. We're excited for the future of ZKPs as it appears to be a critical technological milestone toward building a more decentralized web. And while there remain hurdles to throughput and adoption, ZKPs are helping remake the internet, privacy-first, while pushing forward the adoption of other blockchain applications and use cases.








