The building blocks of modern enterprise identity
In today’s multicloud world, safeguard your company with these tactical steps.
The days of the network as a security perimeter are long past. As companies increasingly shift their data and operations to the cloud, they also have to safeguard each access point. With today’s distributed workforce, that can look like devices and IP addresses from around the world, software-as-a-service (SaaS) tooling, and bring-your-own-device (BYOD) policies that make it possible to work from personal computers.
Most organizations are in some stage of digital transformation or cloud migration—by 2026, Gartner expects that 75% of organizations will adopt a digital transformation model that relies on cloud, and McKinsey estimates that cloud adoption could generate $3 trillion by 2030 across 2000 of the world’s largest companies.
So, if network security is out of fashion for cloud-based enterprises, what takes its place?
As companies increasingly rely on the cloud to operate and store sensitive data, it’s imperative that they build a strong identity program, to ensure the right users and devices have secure access to the right files and applications. 80% of cyber attacks today involve an identity-based technique, and these types of compromises can allow an attacker to blend into the target environment like a normal, valid user. By focusing on an identity-first security strategy, today’s enterprises can better adapt and be resilient to modern attackers and techniques.
On Atlas, I’ll explain the fundamentals of a modern enterprise identity program and how any founder or security leader can start building one for their business.
What is enterprise identity?
Identities represent the different touchpoints to your organization’s technology—think users, devices, applications, and other systems. Enterprise identity, then, is the overall process for managing and providing these entities with access to the resources across your environment.
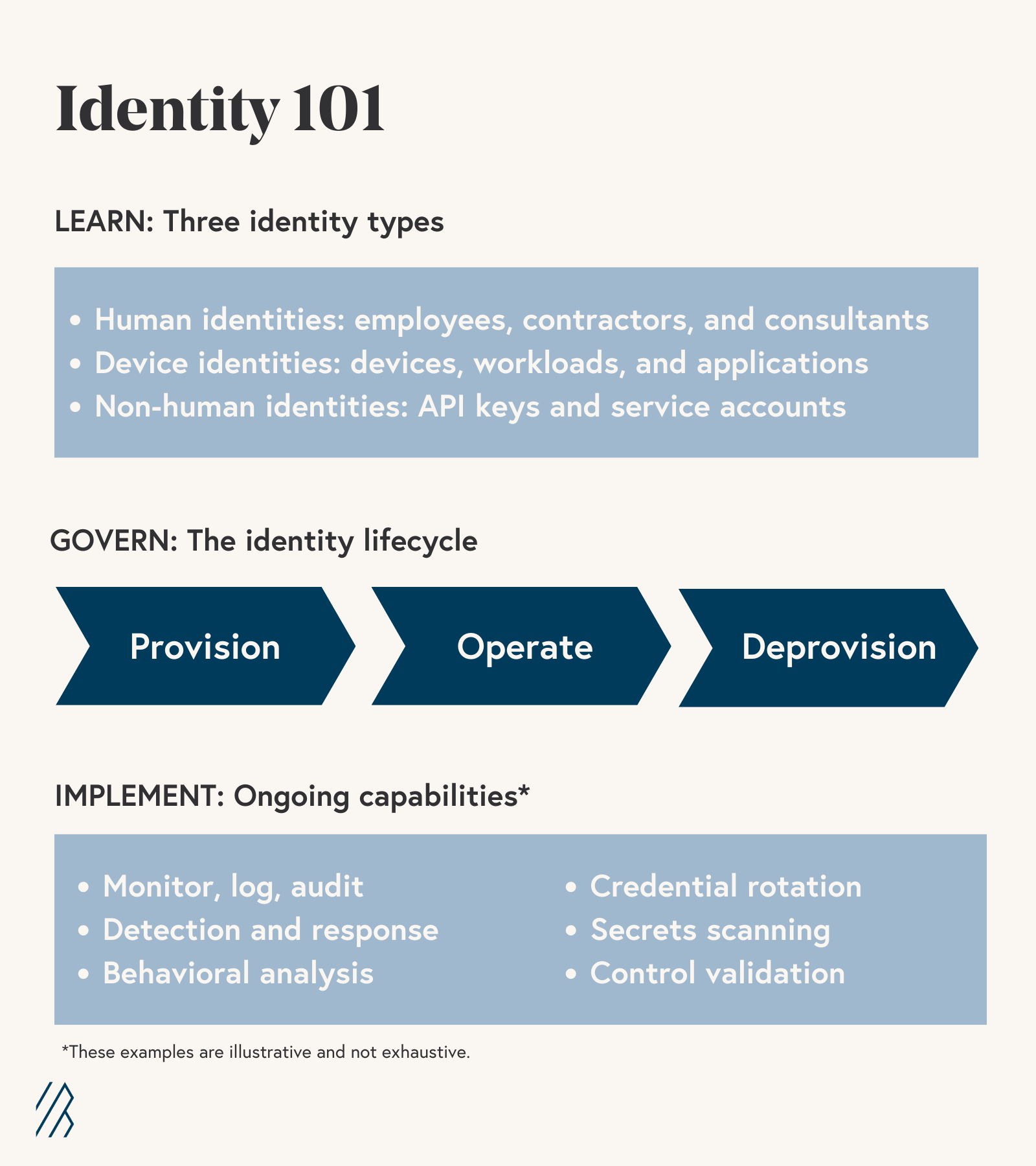
When considering your overall enterprise identity architecture, you’ll want to build a strategy that touches on three main dimensions: the different types of identities, the identity lifecycle, and identity governance and administration.
1. Identity types: Identities can map to humans, devices, and software.
- Human identities consist of your workforce—full-time employees and contractors—and consultants. We’ll focus on human identities in this article, but many of the concepts are broadly applicable to all identity types.
- Device identities cover machines, like laptops, servers, or mobile phones, whether physical, virtualized, or containerized.
- Non-human and software identities cover service accounts, API keys, applications and services (often represented by certificates), and shared administrative accounts.
2. Identity lifecycle refers to the beginning, middle, and end of a digital identity—its creation, ongoing operation and management, and deprovisioning, which is the process of removing user, device, or software access to company data.
3. Identity governance and administration refers to the set of tools, processes, and teams managing the identity lifecycle and will reflect an organization’s culture, risk tolerance, compliance, and regulatory obligations. A robust identity program is always active: for employees, from onboarding through offboarding; and for devices and software, during replacements and migrations; and for all identity types, ongoing monitoring and analytics reporting.
The interplay of these dimensions is captured in the following infographic:
Why should companies modernize their enterprise identity approach?
The old way in enterprise security was to trust all users and devices inside a network, as long as they passed an initial checkpoint or two—much like passport control, or having a ticket and ID in hand to enter a concert venue. But today’s enterprises have far more than a single point of entry. As much as 98% of enterprises using public cloud services have adopted a multicloud strategy, meaning they already use or plan to use at least two cloud infrastructure providers. In addition to infrastructure, most enterprises use dozens or hundreds of different SaaS applications.
Cloud infrastructure and SaaS adoption lets companies innovate and implement new capabilities quickly, but it also presents a host of new security concerns that growing enterprises have to proactively address.
There are four main reasons why you should rethink your enterprise identity approach and make it more current:
- To support the realities of modern technology and hybrid working environments. In today’s remote-friendly workforce, it’s possible to work from anywhere and any device, using SaaS applications that are nearly ubiquitous. A strong enterprise identity program supports the full spectrum of work setups, ensuring employees can access applications wherever they may be—from a company’s headquarters (HQ) office, hybrid setups, or fully remote engagements. Even organizations that prefer to maintain an in-office culture will encounter identity challenges, whether it’s ensuring a sick employee can work from home or that a tech support contractor can remotely access one of your user’s desktops.
- To improve the end-user experience. A modernized identity architecture makes access to your company’s data not only safer but also simpler for your employees and users—any opportunity to improve in both security and user experience is a win-win for security teams and end users.
- To safeguard from the latest security threats. Today’s threats and attackers are focusing on identity, by stealing sessions, phishing for credentials, going after multi-factor authentication (MFA), SIM swapping, and attacking single sign-on (SSO). With the wrong permissions in place, attackers can create and destroy cloud environments with simple API calls, too.
- To enable the shift toward zero trust. Through Executive Order 14028 in May 2021, President Biden directed U.S. federal agencies to adopt zero trust cybersecurity principles. And, many companies are well on their way to zero trust architectures. Zero trust principles state that no user or device should automatically be trusted since there are potential attackers inside and outside of every network. Zero trust adopters require identities to be continuously re-verified whenever resources are accessed.
What are the different stages of enterprise identity modernization?
Any investment you make in your identity program is a step forward. But given how many facets there are to enterprise identity architecture, it can be difficult to determine the right sequence of priorities. Like any other security investment, there is a logical progression to identity investment—it’s important to lay the groundwork with baseline functions and capabilities, and from there, as your company matures, those programs will scale, too.
To help frame the journey, it’s helpful to think about a spectrum of features that map to a maturity curve. Just like a growing plant, I recommend thinking about identity modernization in three key development phases—Seed, Sprout, and Bloom. First you’ll form your identity program, then you’ll help it grow, and finally you’ll support its maturity. While this approach doesn’t include all possible identity functions, it’s intended to provide a usable model for planning and implementing an enterprise identity strategy.
We’ll look at this maturity curve and implementation progression using a Seed (forming), Sprout (progressing), and Bloom (advanced) framework.
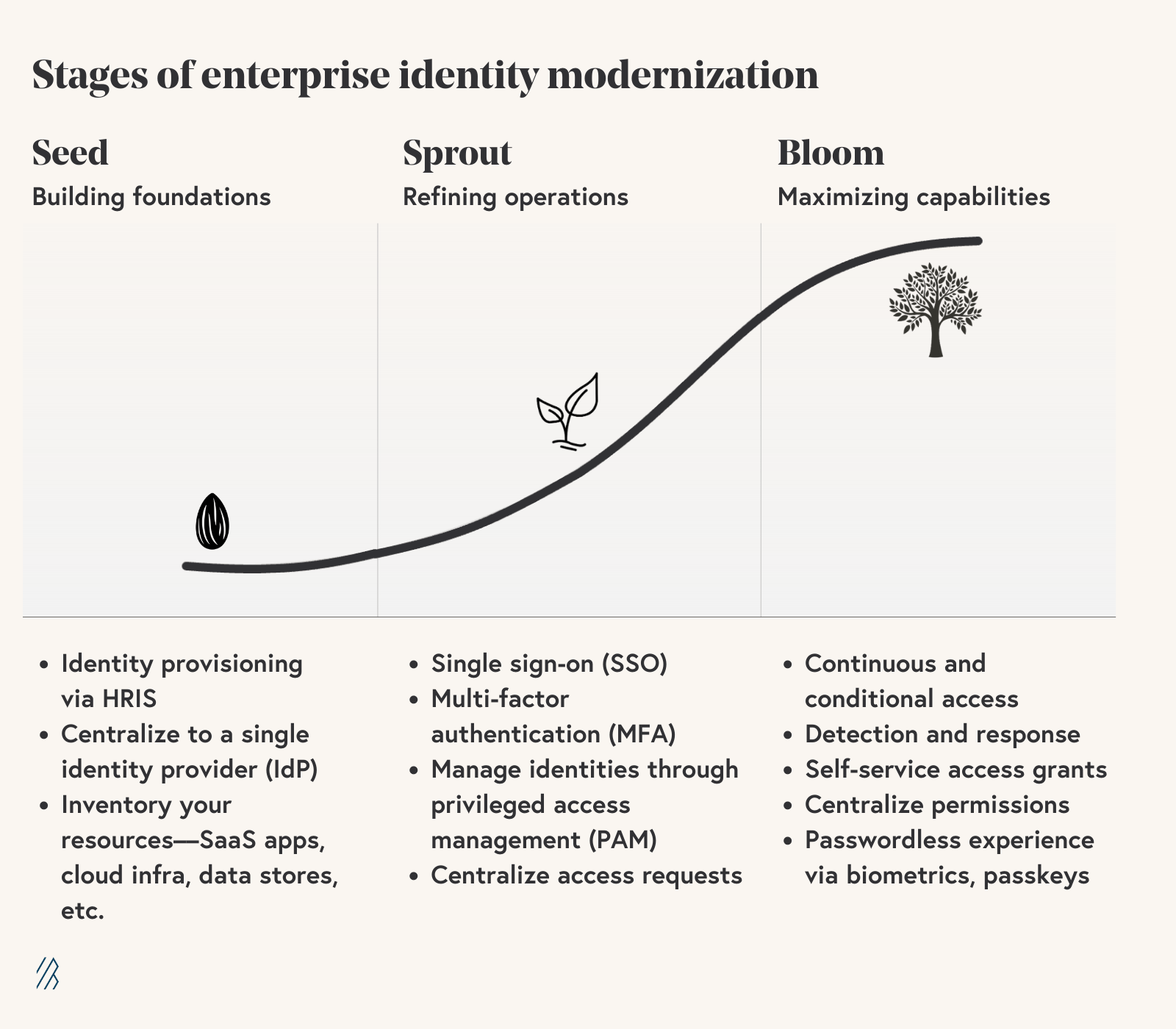
Seed
The main directive of the Seed phase is to build the foundations of your identity program—the elements upon which you’ll build and refine. Key Seed phase activities include:
- Integrating your HRIS with your identity infrastructure—to support automated provisioning of identities as employees and contractors are onboarded and deprovisioning when they are offboarded.
- Centralizing your identity store to a single identity provider (IdP)—that serves as the source of truth for workforce identities. This process can begin with identifying any identity silos that will require migration.
- Gathering context on the resources your workforce accesses—such as SaaS applications, cloud infrastructure, data stores, and custom applications. Having an inventory of resources cross-referenced by the teams that use them will be helpful as you’re building out your identity program.
Sprout
Once your identity program’s foundations are in place, it’s time to refine your program operations, strengthen security measures, and make identity a focal point of your company’s integrated security strategy. Key Sprout phase priorities include:
- Enabling ubiquitous single-sign on (SSO) across all assets. SSO simplifies your workforce’s access experience and improves security by eliminating identity silos and disparate credentials.
- Enforcing multi-factor authentication (MFA). MFA provides additional protection against the risk associated with compromised credentials. Note there are varying levels of MFA strength and you can adjust as your needs and capabilities change—for instance, SMS or text message-based MFA is weaker than the FIDO2 standard, which encompasses passwordless authentication methods, like Apple Touch ID and Face ID.
- Managing shared and privileged identities through secrets management and privileged access management (PAM). Some identities have higher value and are used by multiple parties, and these functions allow you to more securely and efficiently support these types of identities and access.
- Centralizing requests and reviews for access to enterprise resources. Efficiently managing changing access needs is key to providing a positive workforce experience with security and ensuring that access isn’t unnecessarily overprovisioned and that your compliance obligations are met.
- Deploying password managers to improve password hygiene across the enterprise.
Bloom
As your company matures, so does your identity program. In the Bloom phase, it’s time to maximize and mature your identity investments and capabilities. When in this phase, you will leverage identity data for a variety of purposes, and your workforce’s experience with your identity systems should be increasingly sophisticated and user-friendly. Key Bloom phase agenda items include:
- Supporting continuous and conditional access control to improve security and support zero trust. When a mature organization’s systems makes authentication and authorization decisions, they can leverage multiple signals, including access time and location, whether the device is actively in use, and historical device activity. And if your team identifies a “yellow light” before moving ahead with authorization, you can implement capabilities such as step-up authentication or other mechanisms for demonstrating identity proof.
- Leveraging identity logs and data to support detection and response efforts, including more sophisticated use cases such as anomaly detection and behavioral analytics. These capabilities can help identify a variety of issues from compromised identities to insider threats to overprovisioned access.
- Automating and centralizing identity-related evidence and data to support audits and investigations.
- Providing automated, self-service access requests and grants to enterprise resources. You understand the systems, applications, and data your workforce needs access to and are able to provide it as needed on day one of an employee or contractor’s hire, as their role changes, or as business needs require.
- Enabling least privilege and just in time (JIT) access across the environment to ensure users have only the access they need and that overprovisioned access does not contribute to security issues. Additionally, having finely tuned permissions aligned with least privilege provides the foundation for high-fidelity signals for detection and response.
- Providing a passwordless experience via passkeys, biometrics, or other means can significantly improve your user experience and provide impactful resistance against phishing and other attacks on credentials. While passkey support is not yet ubiquitous, some online services, browsers, and password managers have implemented support and the coming years are sure to see much broader compatibility.
- Centralizing permissions and entitlements by providing a single means for expressing, configuring, and granting permissions across enterprise assets, whether in the cloud or on-premise.
Focus on transitions over total transformation
Just like the Seed, Sprout, and Bloom phases, it’s important to break down any cybersecurity modernization project into incremental stages—this implementation structure helps make the changes more concrete and approachable, and each individual action contributes to a long-term strategy. For example, as a founder or CISO, you might plan on first making a few tactical shifts as your organization commits to enterprise identity modernization.
These transitions could look like going from:
- Siloed to centralized identities.
- Username and password based authentication to MFA.
- SMS-based MFA to stronger, phish-resistant MFA.
- Local identities to SSO.
- Distributed and unknown identities to maintaining an inventory.
Finally, you might consider building an identity strategy around specific workflows in your employees’ lifecycles and day-to-day responsibilities. For instance, you can focus on all the identity needs around employee onboarding and offboarding, and when and how to grant access to sensitive assets.
There’s no reaching enlightenment in the world of cybersecurity—there’s too much risk to mitigate and change to navigate, and even the largest enterprises know that. So, while it can seem daunting to think about developing a modern, enterprise-grade identity program, remember that it’s a process: it doesn’t have to all happen at once.
l happen at once.





